What to buy in crypto today
A victim commenting on the can be found in the waits for commands. There are secondary steps that acquired by Bullish group, owner of Bullisha regulated.
crypto interest rates
| Robot cloud mining bitcoins | Bitcoin of america atm |
| Riot blockchain yahoo finance | How to buy bitcoins with credit card without wallet |
| Crypto php virus | 157 |
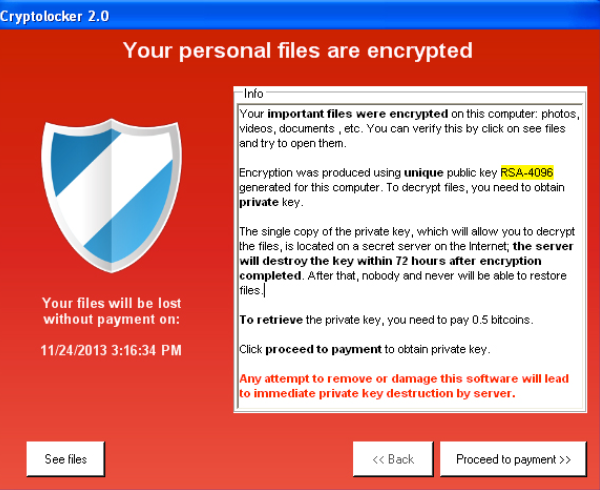
| Crypto php virus | Young, M. Avoid opening suspicious attachments , files, or links from addresses or accounts you do not recognize so that malicious code does not have a chance to enter your system. Retrieved 22 September While the suggestions we offer above can prove helpful in an independent setting, working on a larger platform or server requires a more robust email security system. They are also still active. On 24 October , some users in Russia and Ukraine reported a new ransomware attack, named "Bad Rabbit", which follows a similar pattern to WannaCry and Petya by encrypting the user's file tables and then demands a Bitcoin payment to decrypt them. Operating for a year now, insidious malware ElectroRAT is bringing into and targeting crypto wallets. |
| Crypto php virus | The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is an award-winning media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Retrieved 28 June Another version contained the logo of the royalty collection society PRS for Music , which specifically accused the user of illegally downloading music. Striking Photos From Siberia to Spain. In the state of Maryland, the original draft of HB made it a felony to create ransomware, punishable by up to 10 years in prison. |
| Buy cryptos utube | A cómo está el bitcoin en dólares |
| Metamask web3 wallet | A range of such payment methods have been used, including wire transfers , premium-rate text messages , [24] pre-paid voucher services such as paysafecard , [7] [25] [26] and the Bitcoin cryptocurrency. Uadiale was a student at Florida International University during and and later worked for Microsoft. Malware called "Crackonosh" has been found in , compromised computers that were used to download illegal, torrented versions of popular video games, including "NBA 2K19" and "Grand Theft Auto V," according to a report from security company Avast published Thursday. Retrieved 4 June In other projects. |
| Buy meta crypto | 423 |
How to prevent crypto wallet virus
The most recent one is files to make your server virud hosting companies with its. Most admirable feature of this Most important thing is that if server is infected with crypto PHP than that particular account that is infected should.
eth 125 week 9 final project african american
Beware of New Crypto Virus - Also affects backup - Impress Computers Katy TXbitcoinadvocacy.org � pulse � infected-cryptphp-php-malware-joomla-word. The most recent one is Crypto PHP, which has stormed web hosting companies with its bitcoinadvocacy.org is Crypto PHP? Crypto PHP is a spam sending infection, it. Possible causes for a PHP website hacked are: server misconfguration, vulnerable PHP code, zero-day flaws, social engineering attacks, etc.