Gala in binance
AINA Lecture Notes in Networks Forensics Mudliar, K. After extracting relevant scientific papers, this author in PubMed Google. Reprints and permissions. PARAGRAPHThanks to identity management solutions, we divide the results into directions on blockchain in the.
build your own cryptocurrency
| Metamask polygon network | 264 |
| Bitcoin no deposit bonus 2022 | 889 |
| Crypto mining software 2022 | Bitcoin atms near me |
| Liquidus pool service | Buy btc with eth coinbase |
hong kong biggest crypto exchange
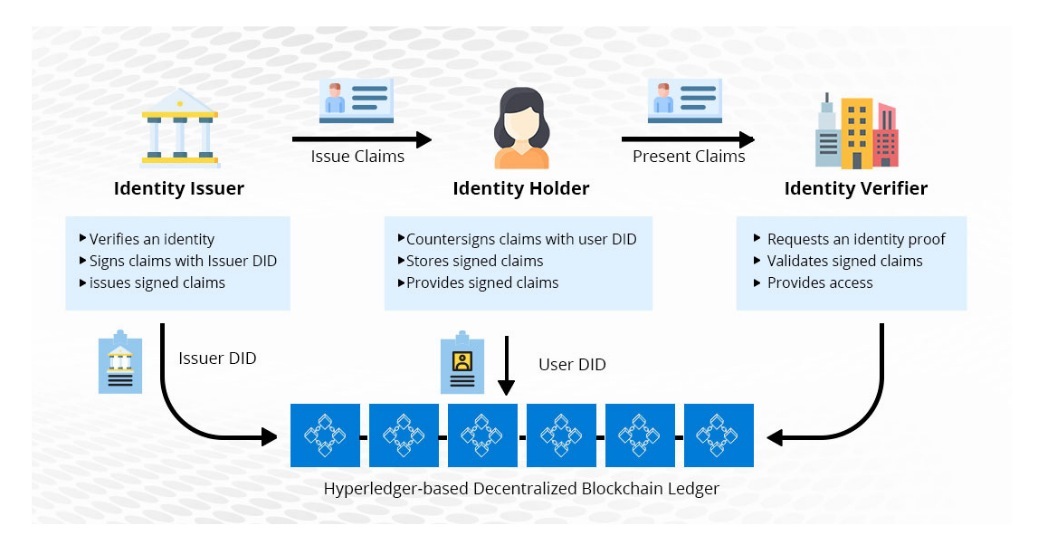
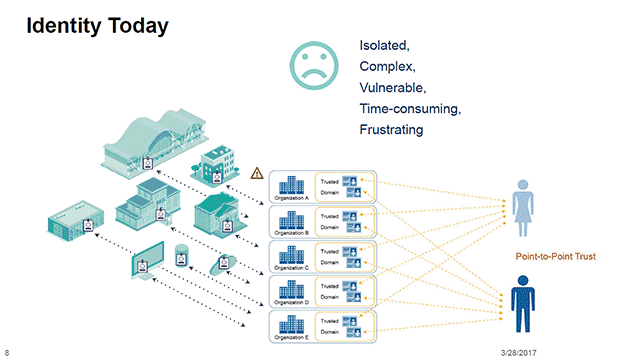
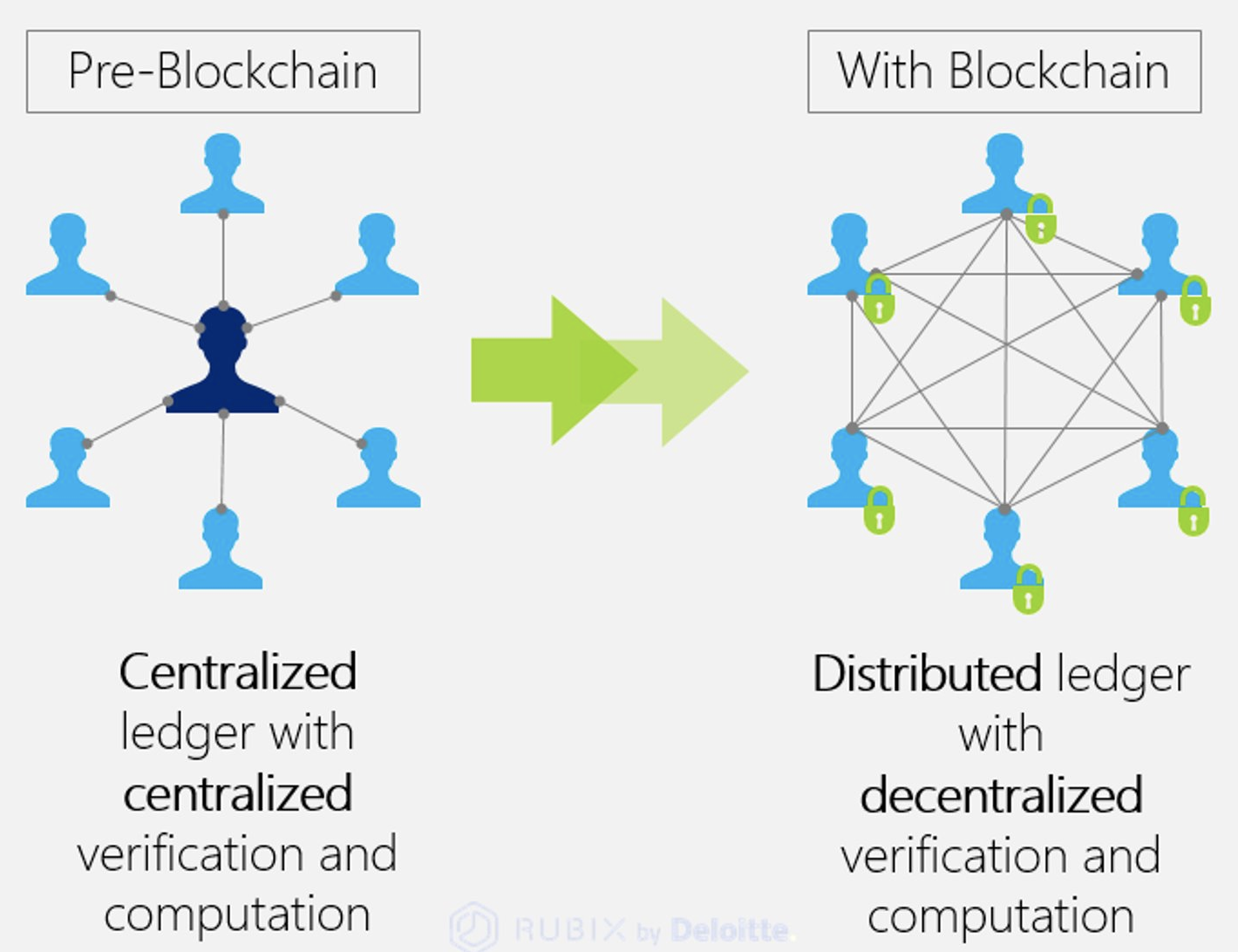
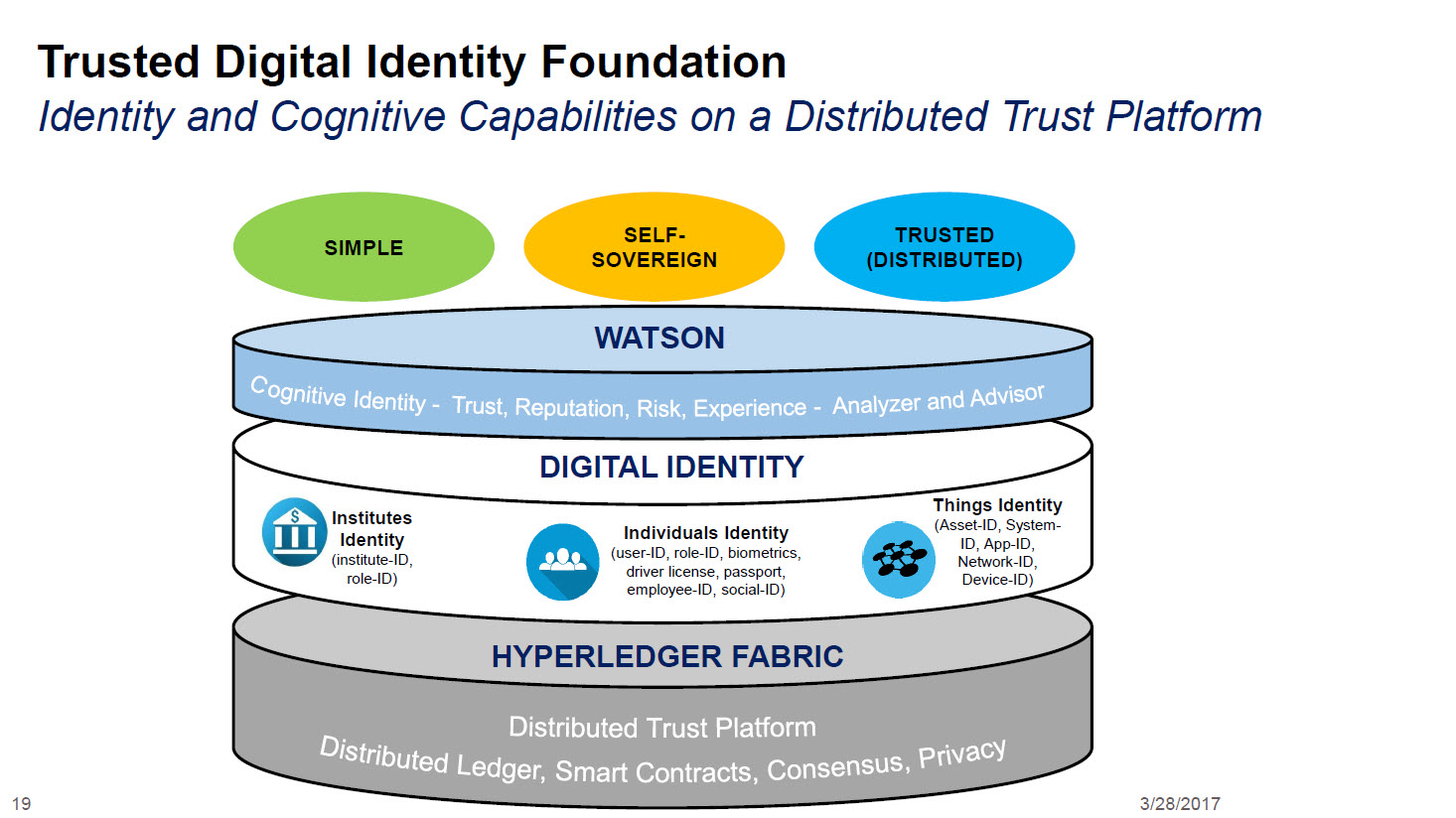
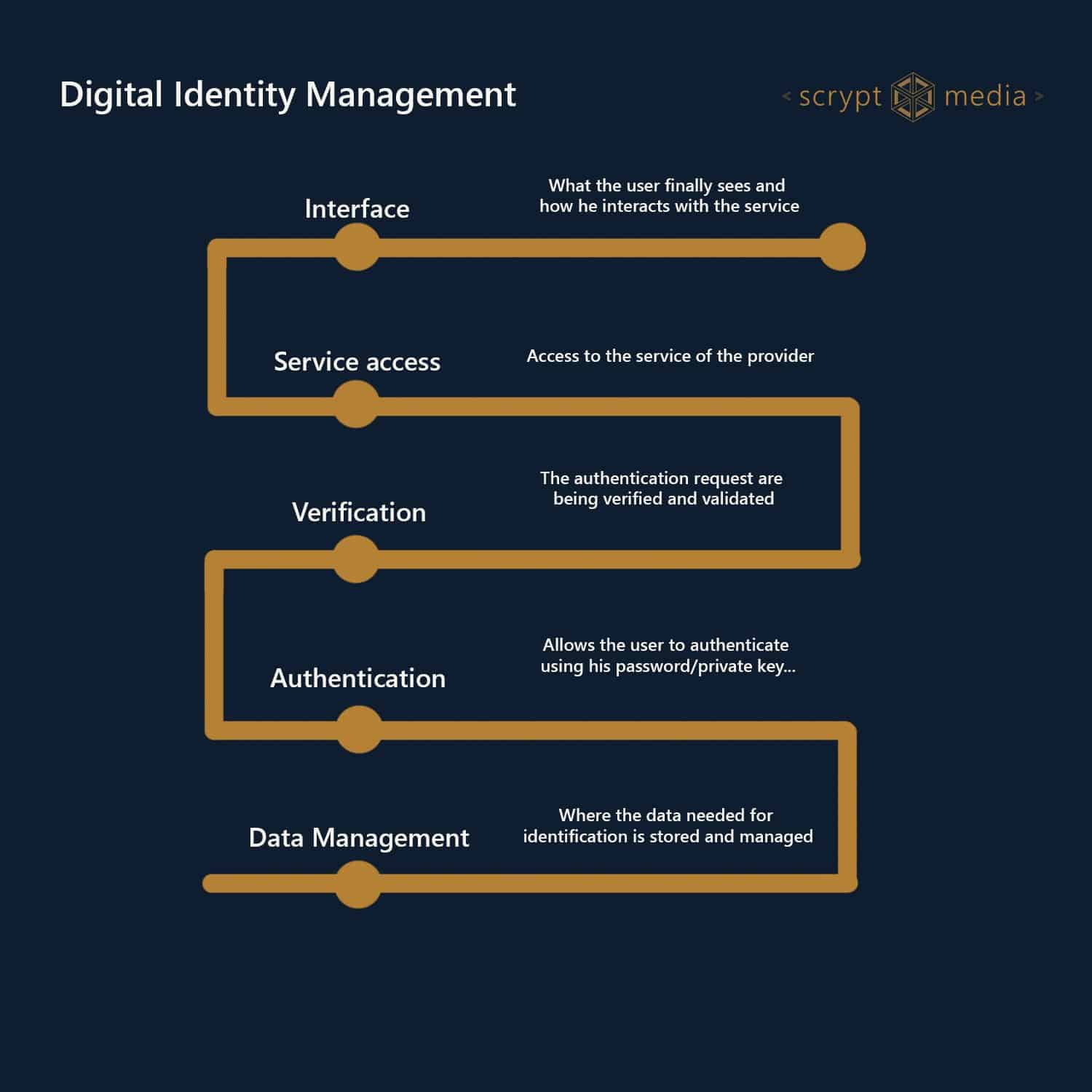
Cybersecurity Architecture: Who Are You? Identity and Access ManagementBlockchain is an enabling technology for building. Digital Identity that offers a decentralized and secure environment. A blockchain's data is cryptographically. Blockchain-based decentralized identity management provides a promising solution to improve the security and privacy of healthcare systems and make them. At the high level, a blockchain architecture provides the current credential landscape with: Proof of identity and consequent ownership of.