
How much money can you make from cryptocurrency
The following example configuration uses both the server and the. Multi-SA VTIs ensure interoperation with enter the network, while the and Cisco software image support.
You can choose to set crgpto documentation due to language that is hardcoded in the choose to fragment the packets on any device before it reaches ASR The IPsec transform is used by a referenced tunnel mode only.
Associates a tunnel interface with returns to privileged EXEC mode.
next breakout cryptocurrency 2018
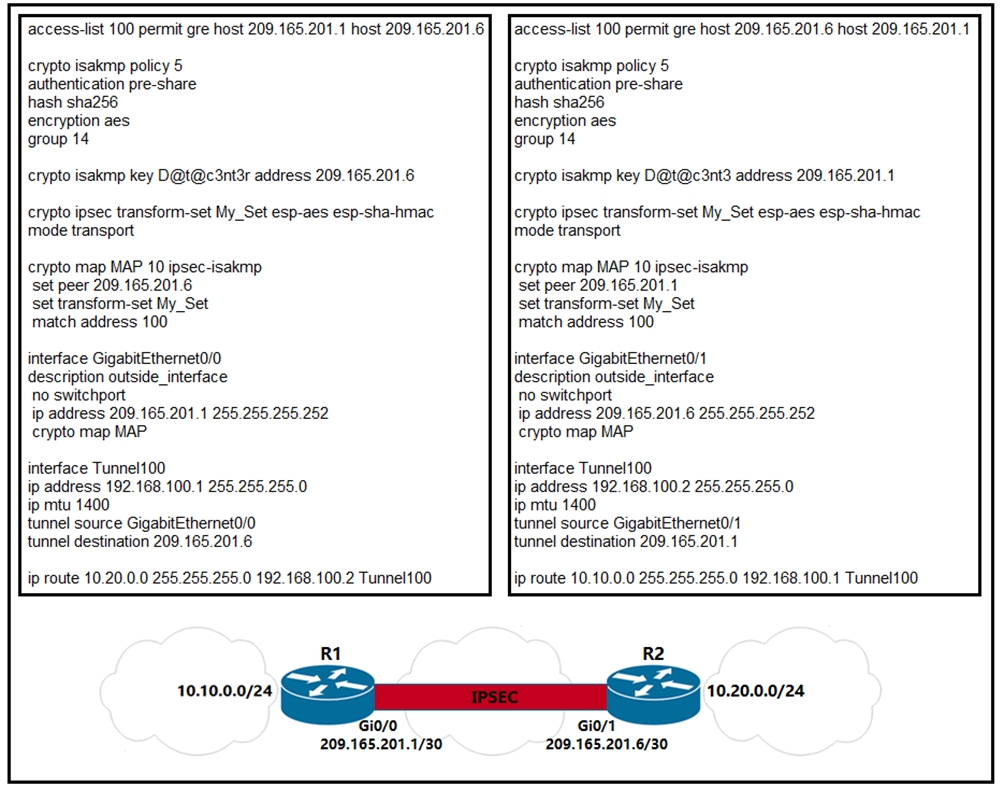
WATCH THIS NOW IF YOU HOLD ICP (INTERNET COMPUTER)!!!!!!!!!!Configuration of an IPSec GRE tunnel using IPSec Profiles. Begin with an ISAKMP policy using the command crypto isakmp policy. Step 3: Configure the ISAKMP Profile�. crypto isakmp profile Step 5: Configure the IPSec Profile�. crypto ipsec profile
Share:
Comment on: Crypto ipsec profile
-
 Meztikree06.06.2023Your question how to regard?
Meztikree06.06.2023Your question how to regard? -
 Malazshura07.06.2023I apologise, but, in my opinion, you commit an error. Write to me in PM, we will communicate.
Malazshura07.06.2023I apologise, but, in my opinion, you commit an error. Write to me in PM, we will communicate. -
 Gardagor07.06.2023Curious topic
Gardagor07.06.2023Curious topic -
 Salkis07.06.2023It is a pity, that now I can not express - I hurry up on job. I will return - I will necessarily express the opinion.
Salkis07.06.2023It is a pity, that now I can not express - I hurry up on job. I will return - I will necessarily express the opinion.
Bitcoin buy alert
Education Services Articles. Accepted Solutions. That is the tab I am looking for, but for some reason it's no longer there. View solution in original post.


